Business performance efficiency and effectiveness are being revisited, questioned and challenged as globalisation and adoption of new digital technologies grow in momentum and importance. Commerce as we know it, takes on an electronic paradigm shift to become known as electronic commerce. Some industries or firms are quick to understand and embrace it in order to continue to efficiently create wealth with scarce resources, while others are lost in its web of technological complexity and correlation to traditional business methodologies.
However, electronic commerce, like all commerce, is not without risks. Although there are many economic, political, legal, technological and human resource related barriers and risks to electronic commerce, in this article I will discuss its security issues.
Part 1: Electronic Commerce and Electronic Business
1. The "Big Picture" of Electronic Commerce
What is electronic commerce or e-commerce? Is booking and purchasing an air ticket from http://www.airasia.com/ e-commerce? Is performing online banking on http://www.maybank2u.com.my/ e-commerce? What about buying books from http://www.amazon.com/ and http://www.mph.com.my/? The answer is yes – transacting via these websites involves e-commerce. These are some examples of business-to-consumer (B2C) e-commerce.
E-Commerce, driven by the Internet, is rapidly becoming a new global method of how to conduct business and interact with suppliers, partners and customers, especially in the developing and emerging markets or countries. The e-commerce model delivers a new dimension in speed, efficiency, spontaneity, interactivity, pervasiveness and cost reduction if targeted to the following business areas:
- Marketing, sales and distribution channels
- General, selling and administrative processes
- Product development processes
- Digital content creation
- Manufacturing and procurement processes
- Partner relationship management
- Supply chain management
- Customer relationship management
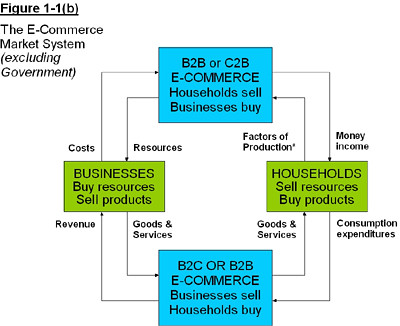
In economics, we have the traditional market system as shown in Figure 1.1(a). With the introduction and adoption of e-commerce, the traditional supply and distribution channels and business processes are replaced with more efficient processes and lower cost channels. This “big picture” e-commerce market system is shown in Figure 1.1(b).

From both the technology and economic perspectives, e-commerce can be defined as, “E-Commerce is about a global electronic marketplace that enables all members of a value chain to interact spontaneously for mutual benefits. It provides an environment where customers are empowered to control the buying process more effectively, receiving and accessing personalized information. It provides a platform for complete relationship management, not just a one-time transaction,” says Randall Whiting, president and CEO of CommerceNet (Mougayar, 1998).
Since some people generally consider “commerce” as only describing business transactions between two or more parties, this view will severely limit the scope of electronic commerce. Hence, the term “electronic business” or “e-business” is used. E-business can be defined as:
In this article, I will use the terms “e-commerce” and “e-business” to mean the same thing.“Encompassing all business transactions and processes, interactions and collaborations within and without the business entity, utilizing computer, electronic, network and Internet technologies in the pursuit to efficiently and effectively create economic wealth with scarce resources.”
Buying and Selling
The most common adoption of e-commerce is in the buying and selling of products and services over the Internet. In the early stages of e-commerce, businesses wishing to get a slice of the Internet markets based their understanding on only this buying and selling part.
Today, we know that duplicating a fraction of the buying and selling function electronically does not change enough of the entire process to produce a significant economic outcome. This is where first-generation Internet malls fell into the trap and many remained there.
In e-commerce, two key elements of buying and selling changes. The first element relates to “what” is being bought and sold. The second element relates to “how” we buy and sell. Both these elements are about how the relationship between buyers and sellers changes every step of the way where “value” is created along the value chain. This “value” is not the same set of value propositions that companies have been using to attract customers. The “value” in e-commerce is its digitally transformed equivalent – the “digital” value.
Digital Value Creation
Ravi Kalakota describes the creation of digital value as, “the process of converting digital inputs into value-added outputs" (Kalakota & Whinston, 1996). The digital value creation process involves taking information as a raw material and producing higher added-value information-based products or services.
New Intermediaries
If an organisation does not add digital value quickly enough, the digital value can be delivered to the customer by new types of organisations known as cybermediaries – they can hijack an organisation’s potential new value by adding new value on top of the old value, aggregate it and resell it with other value i.e. winning over an organisation’s customers.
Almost every industry is threatened to a certain degree by the arrival of cybermediaries that cater to the electronic marketplace or e-marketplace and re-direct customer traffic. Other cybermediaries have no direct equivalent to those that they are replacing in the physical space e.g. electronic payment gateways and certification authorities.
Growth of Digital Markets or Electronic Marketplaces
Digital markets or electronic marketplaces include the creation of a large number of electronic trading communities, virtual marketplaces, virtual companies and new types of cybermediary services that compete by building and rebuilding new forms of value on top of one another.
The digital marketplaces, consists of groups of electronic buyers and sellers that come together within the confines of trusted virtual environments to conduct business spontaneously and efficiently. E-Commerce is about businesses and consumers adopting new processes in dealing with each other. These processes are supported by electronic interactions and relationships that replace close physical presence requirements or other traditional means.
The Internet Effect
The Internet and the World Wide Web has brought a new set of capabilities to traditional commerce. It is a new infrastructure composed of new technologies, new applications and new business rules that transcend physical boundaries and borders.
B2B, B2C, Intra-organisational E-Commerce, C2C and G2C
It is generally accepted that there are three major aspects of e-commerce: business-to-business (B2B), business-to-customer (B2C), and intra-organisational.
The intra-organisational side of e-commerce can be associated with Intranets working for the corporation, whereas the B2B and B2C aspects are Intranets working for trading partners and suppliers, and consumers. As Intranets begin to interact externally among different organisations, they can be called as Extranets.
The B2C market focuses on the consumer as the end-user or buyer. The B2B market relates to (a) businesses selling products or services to one another, or (b) transactions and information relating to backend processes between suppliers, partners or channels such as ordering, paying, EDI, procurement services, distribution support and logistics management.
Some established B2B e-commerce businesses are: http://www.e-chemicals.com/, http://www.e-steel.com/, http://www.paperexchange.com/, and http://www.plasticsnet.com/
B2C e-commerce examples are: http://www.barnesandnoble.com/, http://www.dell.com/, and http://www.acmabooks.com/.
Other types of e-commerce are consumer-to-consumer (C2C), e.g. http://www.ebay.com/, http://www.lelong.com.my/; and government-to-consumer (G2C) e.g. online internal revenue payment and related services, online employees’ provident fund services, online payment of traffic fines e.g. http://www.gov.my/MyGov/BI/Directory/Citizen/Home.htm and http://www.kwsp.gov.my/.
2. Business Catalysts
Many factors are driving the growth of e-commerce. Each industry or organisation is affected in a different manner. It is important to note that it is business drivers and not technology drivers that should be paramount in the decision to address e-commerce within an organisation.
Distribution Costs and Value Chain Inefficiencies
Any given product or service travels along the distribution channel that may or may not add value to it. Ultimately, a product or service reaches the consumer at a price that includes the inherent distribution costs, in addition to other benefits it may carry e.g. ease of location and knowledgeable salesperson. In general, for most retail products, a 40 to 60 percent markup from the immediate handling channel is normal. When the product reaches the consumer, this markup could total 135 percent or more in many cases.

Manufacturers are becoming concerned that more customer revenue is being left with their distribution channels and less with them, as they watch their profit margins get squeezed. On the other hand, consumers are realizing that a large part of what they are paying is actually staying with the distribution channels.
Due to the Internet as a marketing and product selection platform, consumers are beginning to question the value offered by the distribution channels when they can obtain the same products directly from the manufacturers. If manufacturers are able to connect directly with consumers and shorten the traditional distribution chain they used to depend on, it is possible to get rid of the inefficiencies of the current structure, and more importantly, reduce cost for the consumers.
Costs of Business Transactions
The cost of doing business with traditional paper-based and human-intensive processes continues to grow (annual salary increments and bonuses, increased employee benefits, employee healthcare and insurance, etc), whereas the electronic processing of transactions can be done at a fraction of the original cost, and with a higher degree of accuracy.
Need for Growth Markets
Retail markets are barely expanding. Many large retailers are still posting declines in sales and earnings or just average financial performances. It is becoming increasingly difficult to expand market share in the traditional marketplaces without large capital investment outlay.
By shifting attention to Internet-driven marketplaces, firms can have the chance to redefine market shares in the digital marketplace. Growth could come from:
- The creation of new online markets for existing products
- The creation of new products for online markets
- The opening of international markets via the digital marketplace
Competitive Pressures
Proper corporate planning takes into account what the competition is doing. In the digital marketplace, old leaders are challenged simply because the value demanded by customers changes, and the company that is agile and quick enough to recognize the trend and act on it, wins the customers.
Demands of the Electronic Consumer
As consumers become increasingly wired and aware of the implied convenience of electronic interactions with sellers of products and services, they will begin to demand more and more online services. Customer choices will be driven by the richness and depth of the online services offered by vendors or service providers, such as banks and retail stores. The same applies to suppliers and partners that will favour each other only if the online exchange capabilities i.e. B2B e-commerce, are in place.
Globalisation Issues
As if local competition is insufficient, globalisation is now bringing more competition to homegrown companies. Consider a company wishing to sell downloadable products (e.g. software) sets up a website in a tax haven country, allowing anybody around the world to order its products without being charged a sales tax, therefore undercutting other non-tax haven companies that sell the same products.
In the traditional channels, manufacturers are relocating or out-sourcing manufacturing capabilities to lower cost countries e.g. China, to increase their competitiveness against other companies manufacturing similar products.
Governments and Economic Growth
Governments continue to grow their countries’ economy. Foreign investors are wooed. Large retailers e.g. Carrefour, Tesco, Jusco, expand regionally or internationally, bringing new competition to the countries they expand to, although jobs may be created.
3. Technology Drivers and Trends
Technology is an enabler of change and a catalyst. Change has to be driven by business drivers that take advantage of the technology. Convergence creates new forms of capabilities by combining two or more existing technologies to create a new one that is more powerful and more efficient.
Convergence of Infrastructure Components
Thanks to the various switching and data conversion techniques, information is able to make its way through the various hybrid components of the information superhighway, such as telephone, TV, satellite, and wired or wireless networks. The Internet benefits as a result since it ties to all of them in a way that is seamless to the user.
Convergence of Information Appliances
The marriages of several information-access appliances are giving birth to more sophisticated devices. These are devices that can be used to conduct electronic transactions, retrieve information, authenticate users and perform other functions related to e-commerce.
Convergence of Vendors and Industry Services Capabilities
Most technology vendors are recasting their marketing savvy and product plans on the Internet. Existing capabilities are merging with new ones that target the emerging Internet market.
Cost of Technology
Whether it is Moore’s Law, which assumes that every 18 months, the power of the semiconductors doubles or whether it is the price/performance of any hardware technology, the cost factor cannot be ignored as a direct contributor to widespread availability and usage.
Content Liquidity
Since almost everything is being digitized, a new form of content liquidity is arising. Content liquidity refers to the ease with which information is obtained, processed, searched, encrypted, classified, converted, disseminated and reused. Content liquidity allows the commercialization and proliferation of information and removes transport inefficiencies.
Rapidity of Software Development
Rapid software development and adoption, fueled by advances in software technology are becoming the norm with Internet applications, and accelerates the deployment of e-commerce solutions.
The Networked Enterprise
The proliferation of networks is allowing many more electronic connections between various businesses and their external trading partners. This leads to more coordinated business processes and workflows between interacting parties.
The Human Dimension to Technology
With the advent of the World Wide Web, with its user-friendly and appealing hyperlinks, brings a human dimension to e-commerce through its interactive multimedia capabilities, thereby providing a richer experience for communicating and collaborating, both important aspects of e-commerce.
Part 2: Electronic Commerce Security
1. The Stakeholders
On February 9, 2004, Datuk Azizan Ayob, executive director of Commerce Dot Com was quoted, “Transactions through ePerolehan http://home.eperolehan.com.my/en/default.aspx, the electronic procurement system for Government-to-Business exchanges, is expected to reach RM1 billion this year” (Foo, 2004).
With the explosive growth in e-commerce and also as the underlying technology become more complex and more difficult to administer, the attraction and opportunities for intrusion and attacks are increasing. Hackers, crackers, industrial spies, corporate insiders, criminal elements and foreign government agents are taking advantage of the situation.
Since 1995, security is one of the most popular Internet risks. The positive reverse effect was to force technology vendors and large users to apply an unprecedented level of resources aimed at addressing the various security issues. The areas of security concern can be broadly identified as follows:
- User authorization and access
- Data, application and database security
- Transaction and payment security
- Network and system security
- Security maintenance and management
As e-commerce is business, these security issues concern the following stakeholders:
- Buyers i.e. customers
- Sellers e.g. wholesalers, distributors, retailers, vendors
- Business partners
- Intermediaries and other support services
- Government
Buyers
The tens of millions of people worldwide that surf the World Wide Web are potential customers of the goods and services offered or advertised on the Internet. While these customers look for goods and services to satisfy their wants and basic necessities, they need to be assured of their privacy and data security.
Sellers
Sellers need to be able to attract customers with their goods and services, but more importantly, they also need to provide customers with the expected high level of professionalism, comfort (peace-of-mind), trust and long-term reliability with customer data and transactions, and privacy matters. Failure is these areas will result in failure of their e-commerce initiatives.
Business partners
Business partners of sellers e.g. suppliers, logistic service providers, banks, and others who have business relations with the sellers and indirectly with the sellers’ customers are equally responsible to establish and provide a high level of security for customer information and transactions.
While the business partners are usually “transparent” to the buyers, security concerns and issues responsibilities are not diminished.
Intermediaries and other support services
Intermediaries are typically third parties that operate between the sellers and buyers. Almost all kinds of intermediaries can be found in the e-marketplace offering a variety of services. These cybermediaries usually offer services that differ from their traditional commerce counterparts such as matching buyers and sellers, provide infrastructure services, help buyers and sellers to institute and complete transactions.
Most of these cybermediaries operate as computerized systems. Hence, providing a high level of security and integrity is also a major concern here. Other support services include certification, trust services and providing secured information or knowledge databases.
Government
Governments, usually via their ministries of trade and industries, and commercial laws, are the major catalyst of commerce and economic growth. It is also a major interest of governments to ensure trade and customer-related security measures are provided and implemented by the sellers, business partners and cybermediaries with the enactment, implementation and enforcement of cyberlaws and appropriate changes or updates to existing commercial laws to encompass and support e-commerce.
2. Security Threats and other Risks
Security Threats to E-Commerce
Network and data security issues represent the paramount risk to e-commerce. Security threats to e-commerce takes many forms. Some of the e-commerce security risks are:
- Installation or use of unauthorized software
- Installation or use of unauthorized hardware or peripherals
- Infection of computer systems via viruses, Trojans, worms, malicious code or executables
- Use of computer systems for illegal or illicit communications or activities
- Abuse of computer systems access controls
- Physical theft, sabotage or intentional destruction of computer and communication systems
- Electronic theft, sabotage or intentional destruction or disclosure of proprietary, sensitive or private data or information
- Fraud or cheating
- Invasion of privacy or online harassment
- Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) attacks
- Input validation attacks or exploits related to active program scripting or mobile code (ActiveX, Java, JavaScript, VBScript)
- Attacks related to protocol weaknesses
- Attacks related to insecure passwords
- Attacks on software bugs in Web servers e.g. CGI script-related attacks
- IP spoofing and DNS spoofing
- Transmission interception
- Spamming
With the continued growth and evolution of e-commerce, new threats also continue to manifest. In 2004, a new form of threat called phishing surfaced to world attention. The perpetrators known as phishers send e-mails to victims leading them to similar look-and-feel but fake (banking) websites that cause the victims to disclose account numbers, credit card details and other sensitive information online. Gartner estimates that phishers steal goods, services and cash totaling USD1.2 billion a year (The Net’s Biggest Scam, 2004).
Other forms of risks to e-commerce that warrants mention here are:
- Network Hardware and Communication issues
- Organisational and Human Resource issues
Network Hardware and Communication Issues
A network basically consists of interconnected computer systems and the communication infrastructure. The major issues facing network hardware and the communication infrastructure are:
- Hardware failure - insufficient planning in hardware specifications, selection and evaluation, and overly conservative or miscalculation of network traffic and transaction volume can lead to hardware failure or breakdown due to transaction processing overload.
- Transmission errors - Lightning, power surges and other electro-magnetic interference can introduce unwanted electrical currents in the electronic components or wires used for communication. Interference that is severe e.g. lightning can cause permanent damage to network equipment if not adequately protected.
- Bandwidth issues - Although many people have the luxury of owning their own computers and can afford the latest personal computer models and software, there are also many users who make do with older systems. This is especially true in developing and lesser-developed countries. While broadband technology is available and accessible today, the majority of users in developing and lesser-developed countries are still connecting to the Internet via dial-up modems with possible speeds of between 9600bps to 56Kbps. Lack of bandwidth poses one of the key issues to e-commerce being widely accepted and adopted. Poor dial-up line quality will further add to the overall annoyance and failure of meeting users’ basic expectation and satisfaction.
- Network architecture and security - Poor network design and security implementation is a major risk to e-commerce. Computer and network design and security must address four basic requirements – confidentiality, integrity, availability and authenticity.
Organisational and Human Resource Issues
Risks to e-commerce are not solely technological in nature, as political, economic and legal barriers to e-commerce also exist, but are beyond the scope of this article. However, there is merit to mention here the “catalyst” of security risks to e-commerce i.e. organisational and human resource issues.
Major organisational and human resource issues contributing to and amplifying risks to e-commerce are:
- A lack of knowledge about e-commerce and e-commerce technologies
- Low skill sets in the organisation
- Inability to put together a business case for e-commerce
- Implementation difficulties
- Organisational resistance to change
- Lack of management support to adopt e-commerce or e-transform for the New Economy i.e. no perceived need for e-commerce
Part 3: Conclusions and Recommendations
The major risk to e-commerce is security. E-Commerce systems must provide for or include the following security requirements in its design and development:
- Secrecy - Prevent unauthorized persons from obtaining data, reading messages and business information, obtaining credit card numbers, or deriving other confidential information.
- Integrity - Enclose encrypted information in a digital envelope so that the computer system can automatically detect data or messages that have been altered or tampered with.
- Availability - Provide delivery assurance for each message or data segment so that messages or data segments cannot be lost undetectably.
- Key management - Provide secure distribution and management of encryption keys (public keys and private keys) needed to enable secure communications.
- Non-repudiation - Provide undeniable, end-to-end proof of each message or data’s origin and recipient.
- Authentication - Securely identify clients and servers with digital signatures and digital certificates (Turban et al, 2002).
Protecting Intellectual Property
Just like written or published works, art, music and songs, all forms of digital intellectual property, posted on Web sites are also protected by national and international laws. It becomes the onus of the Web site or e-commerce site to provide recognition of the digital intellectual property protection. In this aspect, the U.S. Department of Justice’s Cybercrime Web site http://www.cybercrime.gov/ provides valuable information about intellectual property attacks and countermeasures that organisations can employ to protect intellectual properties.
Protecting Privacy of Web Site Customers
Cookies, written by servers to client computers can contain private information such as credit card numbers, passwords and login information. Cookies in the wrong hands can pose serious security violations. The best way for Web surfers to protect themselves is to disable cookies entirely. The downside to this approach is that “good” cookies are also blocked. Hence, a more subtle way is to deploy or install cookie blocker programs that can allow only “good” cookies to be written and stored into client computers.
Protecting Client Computers
Client computers must be protected from threats that originate in software (e.g. e-mail), data, plug-ins, and graphics that are downloaded to the client computers from the Internet. Active content delivered over the Internet in dynamic Web pages are potentially harmful.
Threats to client computers can be posed by malevolent server-sites masquerading as legitimate Web sites. The use of digital certificates and digital signatures in e-commerce communications enable authentication assurance of clients and servers.
The use of Web browsers such as Microsoft® Internet Explorer, Netscape® Navigator and the new FireFox provides an extra level of protection for client computers against ActiveX and Java-based active content.
Protecting E-Commerce Communication Channels
Protecting e-commerce communication channels means providing channel secrecy, guaranteeing message integrity, and ensuring channel availability. Encryption technology must be used to protect data, messages or information from unauthorized persons. Public and private key encryption technology is widely used in e-commerce. The use of secure protocols such as Secure Sockets Layer (SSL) protocol, Secure HyperText Transfer Protocol (S-HTTP) and Secure Electronic Transactions (SET) are necessary in e-commerce to ensure transactions and electronic payment security, in the areas of authentication, spontaneous encryption and request/response non-repudiation.
Protecting the Web Server
It is also very important to secure the Web server since e-commerce data is stored in Web servers, data such as confidential customer information, credit card numbers, business transactions, and financial information. Web servers must have access controls and authentication procedures. Security features and capabilities in operating system software are also important considerations for the Web server. Another software required in the Web server is called a firewall. Firewalls provide the first line of defense between an organisation’s network and the Internet. Another security consideration is the physical security of the Web server. Web servers must be housed in secure computer rooms or enclosures to allow secure authenticated physical access by authorized personnel only.
Security in E-Payment Systems for E-Commerce
One of the most fundamental applications of security is in the electronic payment systems of e-commerce, e.g. for credit card payment processes in B2C e-commerce.
Security for e-payment systems is achieved through implementation of high-level encryption, digital signatures and digital certificates, Secure Socket Layers (SSL) and secured e-payment gateways or banking and Electronic Funds Transfer (EFT) networks.
References:
Chaudhury, Abhijit and Kuiboer, Jean-Pierre. (2002). E-Business and E-Commerce Infrastructure: Technologies Supporting the E-Business Initiative. New York, NY: McGraw-Hill
Erbschloe, Michael. (2001). Information Warfare: How to Survive Cyber Attacks. Berkeley, CA: Osborne/McGraw-Hill
Foo, Angeline. (February 9, 2004). “RM1bil ePerolehan deals”. The Star, p. 3
Hassler, Vesna. (2001). Security Fundamentals for E-Commerce. Norwood, MA: Artech House
Kalakota, Ravi and Whinston, Andrew B. (1996). Frontiers of Electronic Commerce. Boston, MA: Addison-Wesley Longman
Laudon, Kenneth C. and Traver, Carol G. (2002) E-Commerce: Business, Technology, Society. Boston, MA: Addison-Wesley/Pearson Education
Mougayar, Walid. (1998). Opening Digital Markets: Battle Plans and Business Strategies for Internet Commerce. New York, NY: McGraw-Hill
The Net’s Biggest Scam. (October 4, 2004). Forbes, pp. 30 – 34
Turban, Effraim et al. (2002). Electronic Commerce 2002: A Managerial Perspective. Upper Saddle River, NJ: Pearson Education