I will use the Microsoft Windows file system for this discussion simply because Windows is the most commonly used operating system in the world today, making it an attractive target for unethical hackers and cyber-criminals.
The Windows NT File System (NTFS)
Microsoft's NTFS file system was introduced with the launch of Windows NT, and is still the file system used by Windows 2000, XP, Vista and the new Windows 7 operating system. The NTFS file system is a major improvement over the previous File Allocation Table (FAT) file system.
The NTFS file system “was designed to include many features, including data recovery, security, fault tolerance, large files and file systems, multiple data streams, UNICODE names, sparse files, encryption, journaling, volume shadow copies, and file compression” (Silberschatz, Galvin & Gagne, 2006, p. 790).
Once a computer system is compromised, unethical hackers and cyber-criminals usually hide their malicious files, instructions or data in the hard disk, using either of two popular methods: (a) low-level formatting, and (b) partitioning.
If the low-level formatting method is chosen, unethical hackers and cyber-criminals typically target the redundant sectors and bad sectors to hide their damaging codes. In the partitioning method, the typical target locations are the partition tables, inner-partition gaps, hidden partitions, deleted partitions, unallocated spaces, and boot records. However, a competent and up-to-date anti-virus and anti-spyware application can identify and act to remove such threats.
A more subtle technique makes use of the multiple data streams (MDS) feature of NTFS. The MDS feature enables multiple independent streams of data to exist in a file. Each stream contains the complete data of the file, for e.g. .doc, .xls, .txt, .zip, etc. Furthermore, the MDS includes a data stream known as Alternate Data Stream (ADS), originally created for compatibility with the Apple Macintosh Hierarchical File System (HFS) but is also used by most application programs and native Windows operating system to store file attributes and for temporary storage of other file related information.
Alternate Data Streams (ADS)
ADS provides the ability to fork file data into other files without affecting their functionality and size or display of file information to file browsing utilities such as the DOS “dir” command and Windows Explorer.
The following steps demonstrate how an unethical hacker or cyber-criminal can make use of ADS to plant malicious codes and launch it later.
Step 1: Using Microsoft Windows XP
- Create the folder 'ADS_Demo' in your hard disk root directory C:\
- Copy and paste the applications Notepad.exe and Mspaint.exe into C:\ADS_Demo
- Your result should be similar to that shown in Figure 1
- For this demonstration, let us assume that the application Notepad.exe is the file created and planted by an unethical hacker or cyber-criminal into your PC or laptop, and contains malicious codes. In other words, assume Notepad.exe is the malicious file
- Take note of the file sizes and date stamps as follows: Notepad.exe = 68KB, 4/14/2008 and Mspaint.exe = 335KB, 4/14/2008
Figure 1: Windows Explorer

Step 2: Create an ADS for the malicious file
- Launch 'Command Prompt' from Start All Programs Accessories
- Change directory to C:\ADS_Demo
- Enter the DOS command 'dir' to list the contents of your ADS_Demo sub-directory
- Your results should be similar to Figure 2
- Again, take note of the file sizes and date stamps as follows: Notepad.exe = 69,120 bytes and Mspaint.exe = 343,040 bytes. No change in the date stamps
- Now, to create an ADS, enter the command 'type notepad.exe > mspaint.exe:notepad.exe'
- Your result at this stage should be similar to Figure 3
- Notice that the file size of Mspaint.exe remains unchanged at 343,040 bytes although we have already embedded 69,120 bytes of the malicious file to it, but the date stamp has changed from 4/14/2008 to 10/11/2009
- A check under Windows Explorer (Figure 4) also shows that the file sizes have not changed at all, but the date stamp of Mspaint.exe is now 10/11/2009
Figure 2: Run Command Prompt & List folder contents

Figure 3: Create an ADS for Notepad.exe (the malicious file)

Figure 4: Windows Explorer

Step 3: Launching the malicious file
- In the Command Prompt window, execute the malicious file using the standard DOS command ‘start’ as follows 'start c:\ads_demo\mspaint.exe:notepad.exe' (Figure 5). On your Windows desktop, the Notepad program (the malicious file) will launch (Figure 6)
- Then launch Task Manager to check which program is running. If your computer system is NOT protected by the latest updates against Windows vulnerabilities, then Task Manager will wrongly report that Mspaint.exe is running instead of Notepad.exe (the malicious file) as shown in Figure 7
Figure 5: Launch Notepad.exe (the malicious file)



Step 4: Delete Notepad.exe (the malicious file)
- Since Notepad.exe is the (assumed) malicious file, we must remove or delete it from our computer system
- In the Command Prompt window, enter 'del notepad.exe' (Figure 8)
- Then enter 'dir' to check whether it has been deleted. The 'dir' command shows only the Mspaint.exe file in the sub-directory (Figure 8). Thus, Notepad.exe was deleted or is it?
- Enter the command 'more <. mspaint.exe:notepad.exe > notepad.exe' and the Notepad.exe (the malicious file) is regenerated as shown in Figure 9, and likewise in Windows Explorer (Figure 10)
- Note that prior to deletion, the date stamp of Notepad.exe (the malicious file) was 4/14/2008 and the date stamp of the regenerated Notepad.exe (the malicious file) has changed to 10/11/2009
- Thus, malicious programs embedded using ADS are difficult to be removed or deleted permanently. The use of appropriate anti-intrusion security solutions is usually required
Figure 8: Delete Notepad.exe (the malicious file)
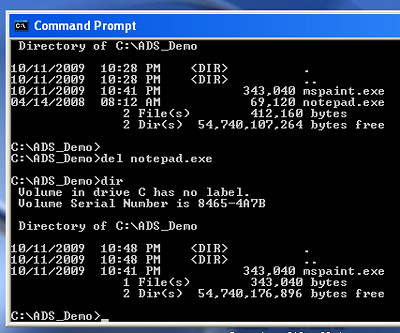
Figure 9: Easily regenerate Notepad.exe (the malicious file)

Figure 10: Windows Explorer

Conclusion
From the above demonstration, we can conclude that when unethical hackers or cyber-criminals gain access to a computer system, they can easily hide malicious programs to existing files, and the file size shows no increase in size even after malicious codes have been added. Later, the malicious programs are launched to cause havoc to the computer system or take control of the computer system to further spread malicious programs to other computers via the Internet.
Therefore, it is important that as a computer user, you ensure that your computer system is:
- updated with the latest updates or patches against operating system vulnerabilities
- protected by a firewall application from a reputable security software company to prevent malicious access or intrusion
- using a firewall program that is regularly updated with any new patches released by the manufacturer (use the auto-update feature)
- protected by an anti-virus and anti-spyware program from a reputable security software company and that the program scans in real-time for viruses, trojans, spyware, malware, etc
- using the latest anti-virus and anti-spyware definition files (use the auto-update feature)
While there are good firewall, anti-virus and anti-spyware programs which are downloadable free-of-charge for use, these typically have some missing or disabled features. For e.g. in most free versions of anti-virus and anti-spyware programs, these solutions do not run in live mode i.e. they allow the computer systems to be infiltrated by the virus or spyware, and then during scheduled scans, take action to clean or remove the virus or spyware. It is highly recommended that you use anti-virus and anti-spyware programs that run live and thus, is able to intercept the incoming virus or spyware in real-time, in addition to scheduled scans.
References:
Gralla, Preston. (2005). Windows XP Hacks, Second Edition. New York: NY, O'Reilly
Silberschatz, Abraham; Galvin, Peter B. & Gagne, Greg. (2006). Operating System Principles, Seventh Edition (Wiley Student Edition). Singapore, John Wiley & Sons Asia
Sinchak, Steve. (2004). Hacking Windows XP. New York: NY, John Wiley
Solomon, David. A. & Russinovich Mark. E. (2000). Inside Microsoft Windows 2000, Third Edition. Redmond: WA, Microsoft Press
Tanenbaum, Andrew S. & Woodhull, Albert S. (1997). Operating Systems: Design and Implementation, Second Edition. Upper Saddle River: NJ, Prentice Hall
Tanenbaum, Andrew S. (2001). Modern Operating Systems, Second Edition (Eastern Economy Edition). New Delhi: India, Prentice Hall India
No comments:
Post a Comment